QUESTION 141
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the Windows Server Update Services roll installed. Server1 stores update files locally in C:\Updates.
You need to change the location in which the updates files are stored to D:\Updates
What should you do?
A. From the Update Services Console, run the Windows Server Update Services Configuration Wizard
B. From the command prompt, run wsusutil.exe and specify the movecontent parameter
C. From the command prompt, run wsusutil.exe and specify the export parameter
D. From the Update Services Console, configure the update Files and Languages option
Answer: B
Explanation:
http://technet.microsoft.com/en-us/library/cc720466(v=ws.10).aspx
QUESTION 142
You have Site1 with 400 desktops and Site2 with 150 desktops.
You have a WSUS Server to deploy updates for both sites.
You need to make sure that all computers in the same site will have the same updates.
What should you configure?
A. Computer Groups
B. Security Groups
C. Synchronization Options
D. Classifications
Answer: A
Explanation:
A. WSUS allows you to target updates to groups of client computers, so you can ensure that specific computers always get the right updates at the most convenient times. For example, if all the computers in one department (such as the Accounting team) have a specific configuration, you can set up a group for that team, decide which updates their computers need and what time they should be installed, and then use WSUS reports to evaluate the updates for the team.
http://technet.microsoft.com/en-us/library/hh328559(v=ws.10).aspx
QUESTION 143
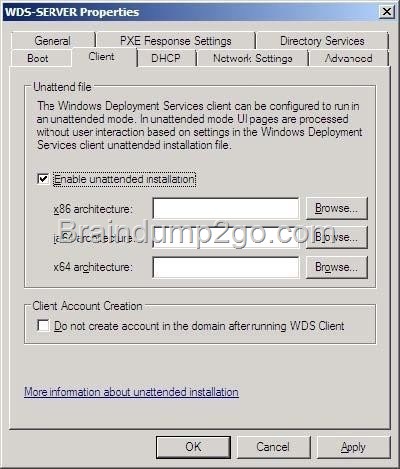
You have a WDS server named Server1 on Windows Server 2012 R2.
You need to automate the WDS deployment.
Which Tab should you configure?
A. Boot Properties
B. Client Properties
C. Network Settings
D. PXE Response Settings
Answer: B
Explanation:
B. On the Client tab, select Enable unattended installation, browse to the appropriate unattend file, and then click Open.
http://technet.microsoft.com/en-us/library/dd637990(v=ws.10).aspx
QUESTION 144
Which parameter do you need to use to import GUID and MAC address?
A. /get-AutoAddDevices
B. /get-Device
C. /add
D. /enable
Answer: B
Explanation:
wdsutil /get-device /id:01-23-45-67-89-AB
wdsutil /get-device /id:0123456789AB
QUESTION 145
Your network contains an Active Directory domain named contoso.com. The domain contains a member server named Server1. Server1 runs Windows Server 2012 and has the Windows Deployment Services (WDS) server role installed.
You need to use WDS to deploy an image to a client computer that does not support PXE.
Which type of image should you use to start the computer?
A. boot
B. install
C. discovery
D. capture
Answer: C
Explanation:
http://technet.microsoft.com/en-us/library/dd637996(v=ws.10).aspx
WDSUTIL /New-DiscoverImage /Image:<name> /Architecture:{x86|x64|ia64} . To specify whichserver the
/DestinationImage /FilePath:<path and name to new file>
discover image connects to, append /WDSServer:<server nameor IP>.
![clip_image001[4] clip_image001[4]](http://examgod.com/l2pimages/f9e6c1207c43_AA19/clip_image0014_thumb.jpg)
QUESTION 146
You are a admin (what a suprise huh?) you have wsus with 2 sites wich contain computers. you want to have the ability to update the computers per site or together. wich 3 steps do you do?
A. Create computer groups in wsus
B. Create synchronization options
C. Create GPO and configure updates
D. Under Tasks, click Synchronize now
Answer: ABC
Explanation:
http://technet.microsoft.com/en-us/library/hh852346.aspx
http://technet.microsoft.com/es-es/library/cc708455(v=ws.10).aspx
QUESTION 147
Which of the options should you configure for a WDS pre-staged computer name? You should select 2 of the 4 check boxes.
A. GUID
B. WdsClientUnattend
C. MAC-address preceding with nulls
D. ReferralServer
Answer: AC
http://technet.microsoft.com/en-us/library/cc754469.aspx
QUESTION 148
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2008 R2.
You plan to test Windows Server 2012 R2 by using native-boot virtual hard disks (VHDs).
You attach a new VHD to Server1.
You need to install Windows Server 2102 R2 in the VHD.
What should you do?
A. Run dism.exe and specify the /apply-image parameter.
B. Run dism.exe and specify the /append-image parameter.
C. Run imagex.exe and specify the /export parameter.
D. Run imagex.exe and specify the /append parameter.
Answer: A
QUESTION 149
You have a server named Admin1 that runs Windows Server 2012 R2.
On Admin1, you configure a custom Data Collector Set (DCS) named DCS1. DCS1 is configured to store performance log data in C:\Logs.
You need to ensure that the contents of C:\Logs are deleted automatically when the folder reaches 100 MB in size.
What should you configure?
A. A File Server Resource Manager (FSRM) quota on the C:\Logs folder
B. A File Server Resource Manager (FSRM) file screen on the C:\Logs folder
C. A schedule for DCS1
D. The Data Manager settings of DCS1
Answer: D
Explanation:
http://sourcedaddy.com/windows-7/using-data-manager-view-performance-data.html
QUESTION 150
Your network contains an Active Directory domain named contoso.com. The domain contains a server named Server1 that runs Windows Server 2012 R2 and a server named Server2 that has the File Services server role installed.
You install the Windows Deployment Services server role on Server1.
You plan to use Server2 as a reference computer.
You need to create an image of Server2 by using Windows Deployment Services.
Which type of image should you add to Server1 first?
A. Boot
B. Discovery
C. Install
D. Capture
Answer: A
Explanation:
A. Configure the server and add the default images (Install.wim and Boot.wim) that are included on the installation media (in the \Sources folder).
B. A type of boot image that you can use to install an operating system on a computer that is not Pre-Boot Execution Environment (PXE) enabled. When you boot a computer into a discover image, a Windows Deployment Services server will be located, and then you can choose the install image you want to install.
C. The operating system image that you deploy to the client computer. To create install images using Windows Deployment Services, you must first create a capture image.
D. A type of boot image that you boot a client computer into to capture the operating system as a .wim file.
You must first create a capture image when you are creating custom install images. http://technet.microsoft.com/en-us/library/cc730907(v=ws.10).aspx http://technet.microsoft.com/en-us/library/jj648426.aspx http://itadmi
ntips.wordpress.com/2011/05/19/wds-setup-guide-part-2-boot-image-setup/
Passing Microsoft 70-411 Exam successfully in a short time! Just using Braindump2go’s Latest Microsoft 70-411 Dump: http://www.braindump2go.com/70-411.html
![clip_image001[87] clip_image001[87]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00187_thumb.jpg)
![clip_image002[62] clip_image002[62]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00262_thumb.jpg)
![clip_image002[64] clip_image002[64]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00264_thumb.jpg)
![clip_image001[89] clip_image001[89]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00189_thumb.jpg)
![clip_image002[66] clip_image002[66]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00266_thumb.jpg)
![clip_image002[68] clip_image002[68]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00268_thumb.jpg)
![clip_image001[91] clip_image001[91]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00191_thumb.jpg)
![clip_image002[54] clip_image002[54]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00254_thumb.jpg)
![clip_image002[56] clip_image002[56]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00256_thumb.jpg)
![clip_image001[81] clip_image001[81]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00181_thumb.jpg)
![clip_image001[83] clip_image001[83]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00183_thumb.jpg)
![clip_image002[58] clip_image002[58]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00258_thumb.jpg)
![clip_image002[60] clip_image002[60]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00260_thumb.jpg)
![clip_image001[85] clip_image001[85]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00185_thumb.jpg)
![clip_image001[65] clip_image001[65]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00165_thumb.jpg)
![clip_image001[67] clip_image001[67]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00167_thumb.jpg)
![clip_image001[69] clip_image001[69]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00169_thumb.jpg)
![clip_image001[71] clip_image001[71]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00171_thumb.jpg)
![clip_image001[73] clip_image001[73]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00173_thumb.jpg)
![clip_image002[38] clip_image002[38]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00238_thumb.jpg)
![clip_image002[40] clip_image002[40]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00240_thumb.jpg)
![clip_image002[42] clip_image002[42]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00242_thumb.jpg)
![clip_image002[44] clip_image002[44]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00244_thumb.jpg)
![clip_image001[75] clip_image001[75]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00175_thumb.jpg)
![clip_image002[46] clip_image002[46]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00246_thumb.jpg)
![clip_image002[48] clip_image002[48]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00248_thumb.jpg)
![clip_image002[50] clip_image002[50]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00250_thumb.jpg)
![clip_image002[52] clip_image002[52]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00252_thumb.jpg)
![clip_image001[77] clip_image001[77]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00177_thumb.jpg)
![clip_image001[79] clip_image001[79]](http://examgod.com/l2pimages/81e1d59efa0a_7768/clip_image00179_thumb.jpg)
![clip_image002[6] clip_image002[6]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0026_thumb_5.jpg)
![clip_image001[6] clip_image001[6]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0016_thumb_5.jpg)
![clip_image001[8] clip_image001[8]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0018_thumb_5.jpg)
![clip_image001[10] clip_image001[10]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00110_thumb_5.jpg)
![clip_image001[12] clip_image001[12]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00112_thumb_5.jpg)
![clip_image001[14] clip_image001[14]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00114_thumb_4.jpg)
![clip_image002[4] clip_image002[4]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0024_thumb_5.jpg)
![clip_image001[4] clip_image001[4]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0014_thumb_5.jpg)
![clip_image001[24] clip_image001[24]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00124_thumb_3.jpg)
![clip_image002[6] clip_image002[6]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0026_thumb_4.jpg)
![clip_image002[8] clip_image002[8]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image0028_thumb_4.jpg)
![clip_image002[10] clip_image002[10]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00210_thumb_3.jpg)
![clip_image002[12] clip_image002[12]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00212_thumb_3.jpg)
![clip_image002[14] clip_image002[14]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00214_thumb_3.jpg)
![clip_image001[26] clip_image001[26]](http://examgod.com/l2pimages/2edfea847c6e_7912/clip_image00126_thumb_3.jpg)
![clip_image001[54] clip_image001[54]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00154_thumb.jpg)
![clip_image002[46] clip_image002[46]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00246_thumb.jpg)
![clip_image001[56] clip_image001[56]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00156_thumb.jpg)
![clip_image001[58] clip_image001[58]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00158_thumb.jpg)
![clip_image001[60] clip_image001[60]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00160_thumb.jpg)
![clip_image001[44] clip_image001[44]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00144_thumb.jpg)
![clip_image001[46] clip_image001[46]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00146_thumb.jpg)
![clip_image001[48] clip_image001[48]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00148_thumb.jpg)
![clip_image002[30] clip_image002[30]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00230_thumb.jpg)
![clip_image002[32] clip_image002[32]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00232_thumb.jpg)
![clip_image002[34] clip_image002[34]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00234_thumb.jpg)
![clip_image002[36] clip_image002[36]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00236_thumb.jpg)
![clip_image002[38] clip_image002[38]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00238_thumb.jpg)
![clip_image002[40] clip_image002[40]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00240_thumb.jpg)
![clip_image002[42] clip_image002[42]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00242_thumb.jpg)
![clip_image002[44] clip_image002[44]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00244_thumb.jpg)
![clip_image001[50] clip_image001[50]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00150_thumb.jpg)
![clip_image001[52] clip_image001[52]](http://examgod.com/l2pimages/b457c7f9fa20_8250/clip_image00152_thumb.jpg)
![clip_image001[17] clip_image001[17]](http://examgod.com/l2pimages/02fd51a724ed_83C8/clip_image00117_thumb.jpg)
![clip_image001[19] clip_image001[19]](http://examgod.com/l2pimages/02fd51a724ed_83C8/clip_image00119_thumb.jpg)
![clip_image001[1] clip_image001[1]](http://examgod.com/l2pimages/02fd51a724ed_83C8/clip_image0011_thumb.jpg)
![clip_image001[3] clip_image001[3]](http://examgod.com/l2pimages/02fd51a724ed_83C8/clip_image0013_thumb.jpg)
![clip_image001[5] clip_image001[5]](http://examgod.com/l2pimages/02fd51a724ed_83C8/clip_image0015_thumb.jpg)
![clip_image001[7] clip_image001[7]](http://examgod.com/l2pimages/02fd51a724ed_83C8/clip_image0017_thumb.jpg)
![clip_image001[9] clip_image001[9]](http://examgod.com/l2pimages/02fd51a724ed_83C8/clip_image0019_thumb.jpg)
![clip_image001[11] clip_image001[11]](http://examgod.com/l2pimages/02fd51a724ed_83C8/clip_image00111_thumb.jpg)
![clip_image001[13] clip_image001[13]](http://examgod.com/l2pimages/02fd51a724ed_83C8/clip_image00113_thumb.jpg)
![clip_image001[15] clip_image001[15]](http://examgod.com/l2pimages/02fd51a724ed_83C8/clip_image00115_thumb.jpg)
![clip_image002[1] clip_image002[1]](http://examgod.com/l2pimages/02fd51a724ed_83C8/clip_image0021_thumb.jpg)
![clip_image002[3] clip_image002[3]](http://examgod.com/l2pimages/02fd51a724ed_83C8/clip_image0023_thumb.jpg)